Mitigating Layer7 HTTP Flood
Mitigating Layer7 HTTP Flood – This tutorial is regarding mitigation of layer 7 http flood using nginx and fail2ban. In this tutorial we assumed to have installed nginx web server and running well. There are many types of Distributed Denial of Service (DDOS) attacks that can affect and bring down a website, and they vary in complexity and size. The most well known attacks are the good old SYN-flood, followed by the Layer 3/4 UDP and DNS amplification attacks and an HTTP flood attack is a type of Layer 7 application attack that utilizes the standard valid GET/POST requests used to fetch information.
Mitigating Layer7 HTTP Flood
Today though, we’re going to spend a little time mitigating Layer 7 HTTP Flood with Nginx+Fail2ban, or what we call an HTTP Flood Attack.
1. Open and edit file nginx.conf
[root@sg03 ]# nano /etc/nginx/nginx.conf
Find http { and paste the lines as below :
limit_conn_zone $binary_remote_addr zone=conn_limit_per_ip:10m;
limit_req_zone $binary_remote_addr zone=req_limit_per_ip:10m rate=100r/s;
limit_req_zone $server_name zone=perserver:10m rate=100r/s;
limit_conn_status 403;
limit_req_status 403;
client_body_timeout 10s;
client_header_timeout 10s;
open_file_cache max=5000 inactive=30s;
open_file_cache_valid 120s;
open_file_cache_min_uses 2;
open_file_cache_errors off;
open_log_file_cache max=1024 inactive=30s min_uses=2;
server_names_hash_max_size 10240;
and then save and closed
2. Now open your virtual host/server block yourdomain.com.conf file located in /etc/nginx or /etc/nginx/conf.d/
[root@sg03 ]# nano /etc/nginx/yourdomain-com.conf
Find location / { and above that add the lines below (add under server block server { )
limit_conn conn_limit_per_ip 10;
limit_req zone=req_limit_per_ip burst=50 nodelay;
limit_req zone=perserver burst=100;
client_body_timeout 10s;
client_header_timeout 10s;
and then save and closed
And restart nginx service
[root@sg03 ]# systemctl restart nginx.service
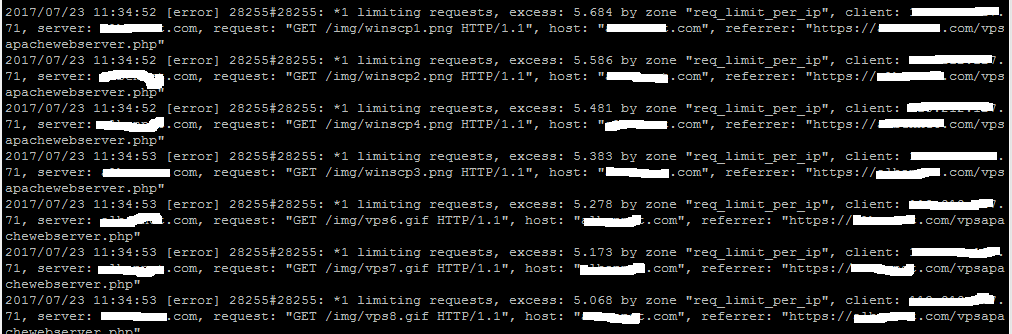
Check your nginx log file to know if connection is being successfully blocked. Blocked connection will have 403 error code.
[root@sg03 ]# tail -f /var/log/virtualmin/yourdomain.com_error_log
Noted : I’m using virtualmin planel so, adjust to your error logs file,
Your nginx is now ready to mitigate layer 7 DDOS. Change the above values as needed by your configuration.
1. Install fail2ban
yum install fail2ban -y
cd /etc/fail2ban
cp jail.conf jail.local
Now create two files named nginx-conn-limit.conf and nginx-req-limit.conf in /etc/fail2ban/filter.d
[root@sg03 ]# cd /etc/fail2ban/filter.d
[root@sg02 filter.d]# nano nginx-conn-limit.conf
and insert this code :
# Fail2Ban configuration file
#
# supports: http_limit_zone_conn module
[Definition]
failregex = limiting connections by zone.*client: <HOST>
# Option: ignoreregex
# Notes.: regex to ignore. If this regex matches, the line is ignored.
# Values: TEXT
#
ignoreregex =
save and closed
[root@sg02 filter.d]# nano nginx-req-limit.conf
and insert this code :
# Fail2Ban configuration file
#
# supports: ngx_http_limit_req_module module
[Definition]
failregex = limiting requests.*client: <HOST>
# Option: ignoreregex
# Notes.: regex to ignore. If this regex matches, the line is ignored.
# Values: TEXT
#
ignoreregex =
and then save and closed
Edit jail.local and add the lines below. Adjust to your error logs file with your configured.
[root@sg03 fail2ban]# nano jail.local
and paste this code
[nginx-req-limit]
enabled = true
filter = nginx-req-limit
action = iptables-multiport[name=ReqLimit, port=”http,https”, protocol=tcp]
logpath = /var/log/virtualmin/mydomain.com_error_log
findtime = 300
bantime = 7200
maxretry = 30
[nginx-conn-limit]
enabled = true
filter = nginx-conn-limit
action = iptables-multiport[name=ConnLimit, port=”http,https”, protocol=tcp]
logpath = /var/log/virtualmin/mydomain.com_error_log
findtime = 300
bantime = 7200
maxretry = 30
and then save and closed
Now start fail2ban service
[root@sg03 fail2ban]# systemctl start fail2ban.service
Check fail2ban rules status
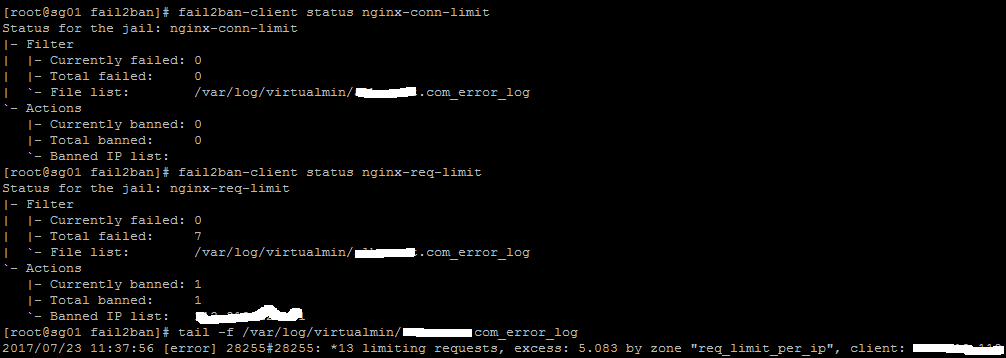
Check fail2ban Log
[root@sg03 fail2ban]# tail -f /var/log/fail2ban.log
Unban IP blocked :
[root@sg03 fail2ban]# fail2ban-client set nginx-req-limit unbanip IP-Blocked
[root@sg03 fail2ban]# fail2ban-client set nginx-req-limit unbanip 11.22.33.44
Your fail2ban is now configured to monitore nginx error log file and ban the IP,
Good Luck


